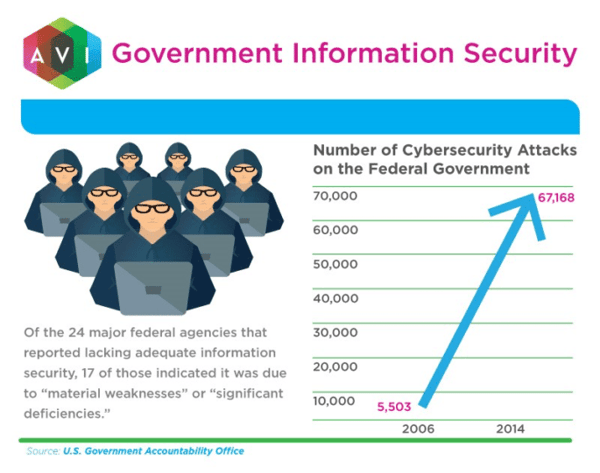
Last year, Chinese hackers accessed the information of 4 million U.S. federal employees. Hackers also infiltrated IRS systems to steal the information of more than 300,000 taxpayers.According to the U.S. Government Accountability Office, attacks increased more than 1,100 percent between 2006 and 2014. Cybercriminals will always be interested in government data.IT professionals always have to be at the ready, but the challenge can seem overwhelming as there are so many potential points of attack.
Rapid7 is an IT security firm that tested video conference security in what is now a well-known experiment in the AV industry. The company hacker was able to easily take over video cameras in many conference rooms. Though the test focused on corporate boardrooms, it served as a warning to everyone in AV and IT. While security is absolutely necessary for government, these agencies often have to struggle to catch up to the technologies used in enterprise. Unfortunately, the lag combined with the crucial need for security creates a bind.
To prevent a breach, IT has to address potential weaknesses in transmission, at every endpoint, and in every layer. From firewalls, to encryption, to record-keeping, and human vulnerabilities, there is a lot to consider, right down to your camera covers. And since many organizations don’t even discover breaches until much later, they need to worry about detection after the fact, in addition to threat prevention.
Government and enterprise can learn from each other in the ongoing cyberspace security battles with hackers. IT security is much more complicated than whether IT employees had the understanding or the concern to protect your agency’s data. There will never be a time when IT can sit back and say their job is done with securing all the technologies in their care. As hard as they work to secure them, the hackers are working to breach them.
That’s why a knowledgeable integration partner can help. They can piece together your puzzle of hardware and software technologies in a safe, secure way.








